Beware of Fake CAPTCHA Challenges
Arctic Wolf (Unified Security Operations), a TCT IT vendor, has recently observed a campaign in which threat actors compromise widely used websites across various industries by embedding a fake CAPTCHA challenge.
How it works:
When victims visit the site, they are presented with the CAPTCHA challenge, or redirected to a site that provides instructions, triggering PowerShell code execution and ultimately leading to the loading of information-stealing malware.
Some recent examples of cases observed by Arctic Wolf, where websites were compromised and had an embedded fake CAPTCHA challenge, include:
- A popular physical therapy video site, HEP2go
- Several auto dealership websites
At this time, Arctic Wolf is unaware of when the compromised websites will be fixed and strongly recommends avoiding sites that present a fake CAPTCHA challenge until the issue is resolved.
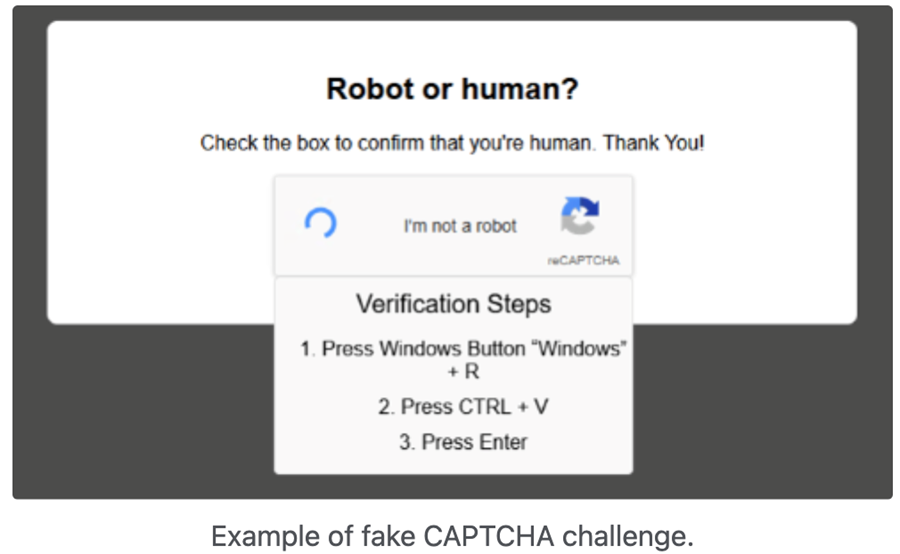
Legitimate CAPTCHA challenges do not require users to copy a command or output and paste it into the Windows Run dialog box.
If the challenge resembles the example above, the website is likely compromised and should not be visited.
« Return to "TCT Blog"




